Behind the Screens: Exposing the Diverse Range of Daily Cyber Attacks
In today’s interconnected world, where technology permeates every aspect of our lives, the threat of cyber attacks looms large. Behind the screens, a vast array of cybercriminals and malicious actors are constantly devising new ways to exploit vulnerabilities and compromise our digital security. This blog peels back the layers to expose the diverse range of daily cyber attacks, revealing the tactics and techniques employed by these nefarious individuals.

Diverse Range of Daily Cyber Attacks
Phishing: Hook, Line, and Sinker
Phishing attacks have become alarmingly commonplace, targeting unsuspecting individuals and organizations. Phishing attacks trick users into revealing sensitive information through deceptive emails.
- An estimated 3.4 billion spam emails sent every day.
- Nearly 85% of all emails are spam.
- Roughly 100 million phishing scams are blocked by Google every day.
Malware: The Silent Intruder
Malware, such as viruses and ransomware, infiltrates systems to steal data or disrupt operations. Users can inadvertently download malware through infected websites, email attachments, or malicious links.
- Over 350,000 new malicious programs are discovered every day.
- Every minute, four companies fall victim to ransomware attacks.
- A ransomware attack happens every 14 seconds.
DDoS Attacks: Overwhelming the Defenses
DDoS attacks flood servers with traffic, causing service outages. DDoS attacks can cripple online businesses, disrupt critical services, and even bring down entire websites, resulting in financial losses and reputational damage.
- In 2022, the number of DDoS attacks grew 150% on a global basis compared to the previous year.
- DDoS attacks are increasing in size, with the average attack size reaching 5.17 Gbps in Q2 2022.
- In 2022, DDoS attacks resulted in an average loss of $2.3 million per attack for enterprises.
Insider Threats: The Trojan Horse Within
Organizations face not only external threats but also the dangers posed by insiders with malicious intent. Disgruntled employees or contractors with privileged access can cause significant harm by stealing data, compromising systems, or leaking sensitive information.
- In the 2023 Insider Threat Report, 74% of organizations feel moderately to extremely vulnerable to insider attacks.
- Nearly half of organizations said detecting and preventing insider attacks is more difficult than external cyberattacks.
Advanced Persistent Threat (APT) Attacks: Stealthy and Targeted
APT attacks are sophisticated, targeted cyber attacks that infiltrate specific targets over a prolonged period. Conducted by well-funded hackers with political or economic motives, they employ techniques like spear phishing, zero-day exploits, and network lateral movement.
- In 2022, the average cost of an APT attack was $4.8 million, according to a report by Accenture.
- APT attacks can remain undetected for an average of 146 days, giving attackers ample time to exfiltrate sensitive data, according to a 2021 report by Verizon.
SQL Injections: Exploiting Databases
SQL injection attacks involve the insertion of malicious SQL queries through client input, enabling various harmful actions such as data tampering, identity spoofing, and unauthorized access to sensitive information. Attackers can manipulate data, disrupt services, or even gain administrative control over the database server.
- In 2022, the number of SQL injection attacks reported by OWASP was 274,000.
- It takes less than 10 seconds to perform an SQL injection attack on a vulnerable website.
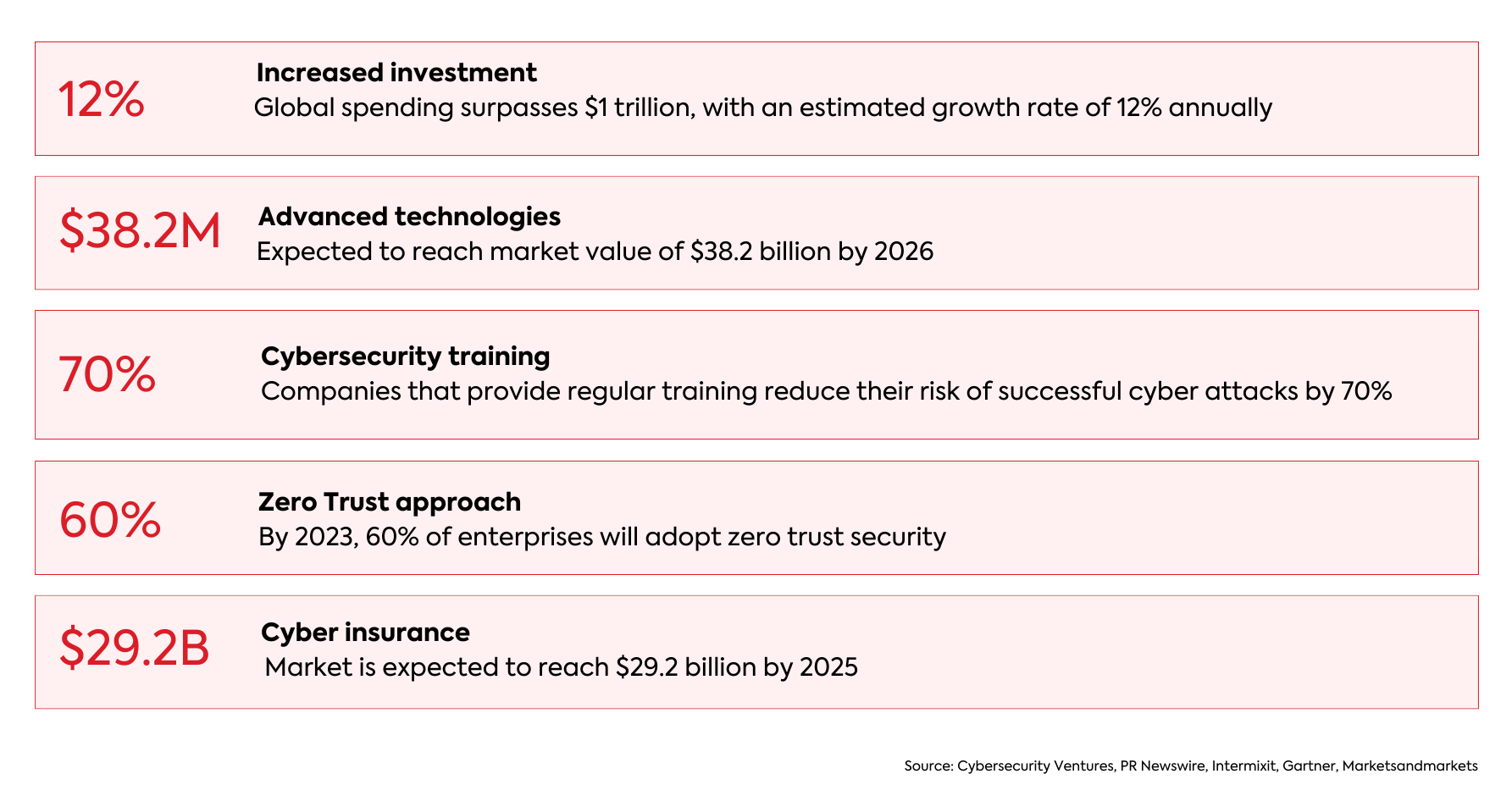
Businesses Combat the Rise in Cyber Attacks:
Conclusion
Cyber attacks are a constant menace, but by understanding their methods, individuals and organizations can enhance their cybersecurity defenses. Implementing measures such as strong passwords, regular software updates, employee training, and proactive monitoring can go a long way in protecting against these diverse daily cyber threats. How to Protect Yourself from Cyber Attacks? Click here
Stay informed, stay secure, and stay one step ahead of the attackers in the digital realm.
Suggested Readings:
The Major Types of Phishing Attacks & How to Identify Them: The Definitive Guide
The Rise of Cybercrime – An Overview
7 Cybersecurity Trends That Every Business Owner Should Be Aware Of
The post Behind the Screens: Exposing the Diverse Range of Daily Cyber Attacks appeared first on WeSecureApp :: Simplifying Enterprise Security.
*** This is a Security Bloggers Network syndicated blog from WeSecureApp :: Simplifying Enterprise Security authored by Khushboo Chahal. Read the original post at: https://wesecureapp.com/blog/behind-the-screens-exposing-the-diverse-range-of-daily-cyber-attacks/

